目次
iOS12.2リリース。メジャーアップデートなので更新は少し待ったほうが良いかも。アップデートすべき?待つべき?不具合は?サイズ・更新時間・修正内容は?
iOS12.2アップデートすべき?待つべき?
今回のアップデートは2番目の数字が変更されるメジャーアップデートとなります。 最近の傾向として起動しなくなる、通信できなくなるなど、大きな不具合はないと予想されますし、過去の不具合が解消されている可能性も高いです。 が、アップデートファイルのサイズも大きく(私のiPhone XS Max(iOS12.1.4)では840.4MB)、メジャーバージョンアップということもあり、新機能の追加なども含まれています。 なので、新たな不具合が発生しないとも限らないため、ちょっとだけアップデートは待った方が無難かもしれません。iOS12.2にアップデート後の不具合の発生の有無について
2019年3月26日12:00現在、iPhone XS Maxを更新して4時間使いましたが、- 文鎮になる(起動しない)
- 再起動を繰り返す
- 通信できない
- メール
- Facebook Messenger
- LINE
- メモ
- 写真
- SLPRO X
iOS12.2のサイズとアップデート所要時間、パージョンについて
現行iOSのバージョン、また所要時間については通信環境に大きく依存しますが、iOS12.2のサイズとアップデート所要時間ならびにインストール後に表示されるパージョンは次の通りです。| 機種 | 現行iOS | サイズ | 全体 所要時間 | ダウンロード 所要時間 | インストール 所要時間 | バージョン |
|---|---|---|---|---|---|---|
| iPhone XS Max | iOS12.1.4 | 840.4MB | 21分 | 4分 | 17分 | 16E227 |
- 最低30分、できれば1時間以上iPhone/iPadを使用しなくて済む時間
- 電源に接続された環境
- 安定したWi-Fi環境
iOS12.2の修正内容について
iOS12.2はメジャーアップデートということで、不具合、セキュリティへの対応の他に新機能の追加なども盛り込まれています。。 公式サイト「iOS12のアップデートについて」の「iOS 12.2」には次のように記載されています。
公式サイト「iOS12のアップデートについて」の「iOS 12.2」には次のように記載されています。
iOS 12.2全般的には2019年3月26日に行われたアップルのスペシャルイベントの機能・アプリを使いたいときに必要となる更新となっています。 また、今週発売された新しい第2世代のAirPodsを使いたいときも今回のiOS12.2以降が必要となります。 今回のバグ・不具合の修正により、他のバグ・不具合も修正される可能性もあります。iOS 12.2には、4つの新しいアニ文字が追加されました。このアップデートにはバグの修正および改善も含まれます。 アニ文字AirPlay
- iPhone X以降、iPad Pro 12.9インチ(第3世代)、およびiPad Pro 11インチに、4つの新しいアニ文字(フクロウ、イノシシ、キリン、サメ)を追加。
Apple Pay
- コントロールセンターおよびロック画面に専用のTVコントロールを追加し、素早くTVコントロールにアクセスが可能。
- ビデオ用AirPlayマルチタスク機能によりその他のAppを閲覧可能。また、AirPlayを中断せずにデバイス上の短い形式のオーディオ/ビデオファイルを再生可能。
- AirPlay先をコンテンツ内容に応じてグループ化し、再生先のデバイスをより速く見つけることが可能。
スクリーンタイム
- Apple Pay Cashの利用者は、Visaデビットカードを使用して銀行口座に送金が可能。
- Wallet Appで、カードの下にクレジットおよびデビットカードの最近の利用履歴を表示。
Safari
- 休止時間のスケジュールを曜日別に設定可能。
- 新しい切り替え方法により、簡単にAppの制限を一時的にオンまたはオフにすることが可能。
Apple Music
- パスワードの自動入力機能により認証情報を入力したあと、Webサイトに自動的にサインイン可能。
- 暗号化されていないWebページを読み込んだときに警告を表示。
- ユーザ識別のためのフィンガープリントとして利用されるのを防ぐため、トラッキング停止要求(Do Not Truck)機能への対応を削除。インテリジェントトラッキング防止機能により、デフォルトでサイト越えのトラッキングを防止。
- スマート検索フィールドの検索語句を検索候補の横の矢印アイコンをタップして変更可能。
AirPods
- “見つける”タブで、1つのページにエディターからのハイライト情報をより多く表示し、新しい音楽やプレイリストを見つけることが可能。
このアップデートには以下の改善およびバグの修正も含まれます:
- 新しいAirPods(第2世代)に対応。
- “マップ”で、アメリカ、イギリス、インドの空気質指数に対応。
- “設定”に、デバイスの保証期間の有効期限に関する情報を追加。
- “メッセージ”で、オーディオ録音の品質を改善。
- iOS上のApple TV Remoteの安定性およびパフォーマンスを改善。
- 不在着信が通知センターに表示されない場合があった問題を修正。
- 必要がないにもかかわらず、“設定”に操作を促すバッジが表示されることがあった問題に対処。
- “設定”>“一般”>“iPhoneストレージ”で、サイズの大きなApp、システムのカテゴリー、およびその他のカテゴリーがストレージのバー表示で正しく表示されないことがあった問題に対処。
- “ボイスメモ”で、車のBluetoothデバイスに接続すると自動的に録音が再生されてしまうことがあった問題を修正。
- “ボイスメモ”で、一時的に録音の名称変更ができない場合があった問題を解決。
iOS12.2のセキュリティコンテンツについて
iOS12.2では41件のセキュリティ問題への対応が実施されています。 公式サイト「About the security content of iOS 12.2」にはまだ日本語の情報が記載されていないため英語の情報をお知らせします。iOS 12.2Released March 25, 2019 CFStringconfigd
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing a maliciously crafted string may lead to a denial of service
- Description: A validation issue was addressed with improved logic.
- CVE-2019-8516: SWIPS Team of Frifee Inc.
Contacts
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to elevate privileges
- Description: A memory initialization issue was addressed with improved memory handling.
- CVE-2019-8552: Mohamed Ghannam (@_simo36)
CoreCrypto
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to elevate privileges
- Description: A buffer overflow issue was addressed with improved memory handling.
- CVE-2019-8511: an anonymous researcher
Exchange ActiveSync
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to elevate privileges
- Description: A buffer overflow was addressed with improved bounds checking.
- CVE-2019-8542: an anonymous researcher
FaceTime
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A user may authorize an enterprise administrator to remotely wipe their device without appropriate disclosure
- Description: This issue was addressed with improved transparency.
- CVE-2019-8512: an anonymous researcher, an anonymous researcher
Feedback Assistant
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A user’s video may not be paused in a FaceTime call if they exit the FaceTime app while the call is ringing
- Description: An issue existed in the pausing of FaceTime video. The issue was resolved with improved logic.
- CVE-2019-8550: Lauren Guzniczak of Keystone Academy
Feedback Assistant
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to gain root privileges
- Description: A race condition was addressed with additional validation.
- CVE-2019-8565: CodeColorist of Ant-Financial LightYear Labs
file
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to overwrite arbitrary files
- Description: This issue was addressed with improved checks.
- CVE-2019-8521: CodeColorist of Ant-Financial LightYear Labs
GeoServices
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing a maliciously crafted file might disclose user information
- Description: An out-of-bounds read was addressed with improved bounds checking.
- CVE-2019-6237: an anonymous researcher
iAP
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Clicking a malicious SMS link may lead to arbitrary code execution
- Description: A memory corruption issue was addressed with improved validation.
- CVE-2019-8553: an anonymous researcher
IOHIDFamily
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to elevate privileges
- Description: A buffer overflow was addressed with improved bounds checking.
- CVE-2019-8542: an anonymous researcher
IOKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A local user may be able to cause unexpected system termination or read kernel memory
- Description: A memory corruption issue was addressed with improved state management.
- CVE-2019-8545: Adam Donenfeld (@doadam) of the Zimperium zLabs Team
IOKit SCSI
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A local user may be able to read kernel memory
- Description: A memory initialization issue was addressed with improved memory handling.
- CVE-2019-8504: an anonymous researcher
Kernel
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: An application may be able to execute arbitrary code with kernel privileges
- Description: A memory corruption issue was addressed with improved input validation.
- CVE-2019-8529: Juwei Lin (@panicaII) of Trend Micro
Kernel
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A remote attacker may be able to cause unexpected system termination or corrupt kernel memory
- Description: A buffer overflow was addressed with improved size validation.
- CVE-2019-8527: Ned Williamson of Google and derrek (@derrekr6)
Kernel
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: An application may be able to gain elevated privileges
- Description: A logic issue was addressed with improved state management.
- CVE-2019-8514: Samuel Groß of Google Project Zero
Kernel
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to determine kernel memory layout
- Description: A memory initialization issue was addressed with improved memory handling.
- CVE-2019-8540: Weibo Wang (@ma1fan) of Qihoo 360 Nirvan Team
Kernel
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A local user may be able to read kernel memory
- Description: A memory corruption issue was addressed with improved memory handling.
- CVE-2019-7293: Ned Williamson of Google
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to determine kernel memory layout
- Description: An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation.
- CVE-2019-6207: Weibo Wang of Qihoo 360 Nirvan Team (@ma1fan)
- CVE-2019-8510: Stefan Esser of Antid0te UG
Messages
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing a maliciously crafted mail message may lead to S/MIME signature spoofing
- Description: This issue was addressed with improved checks.
- CVE-2019-7284: Damian Poddebniak of Münster University of Applied Sciences
Power Management
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A local user may be able to view sensitive user information
- Description: An access issue was addressed with additional sandbox restrictions.
- CVE-2019-8546: ChiYuan Chang
Privacy
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to execute arbitrary code with system privileges
- Description: Multiple input validation issues existed in MIG generated code. These issues were addressed with improved validation.
- CVE-2019-8549: Mohamed Ghannam (@_simo36) of SSD Secure Disclosure (ssd-disclosure.com)
ReplayKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious app may be able to track users between installs
- Description: A privacy issue existed in motion sensor calibration. This issue was addressed with improved motion sensor processing.
- CVE-2019-8541: Stan (Jiexin) Zhang and Alastair R. Beresford of the University of Cambridge and Ian Sheret of Polymath Insight Limited
Safari
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to access the microphone without indication to the user
- Description: An API issue existed in the handling of microphone data. This issue was addressed with improved validation.
- CVE-2019-8566: an anonymous researcher
Safari Reader
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A website may be able to access sensor information without user consent
- Description: A permissions issue existed in the handling of motion and orientation data. This issue was addressed with improved restrictions.
- CVE-2019-8554: an anonymous researcher
Siri
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Enabling the Safari Reader feature on a maliciously crafted webpage may lead to universal cross site scripting
- Description: A logic issue was addressed with improved validation.
- CVE-2019-6204: Ryan Pickren (ryanpickren.com)
- CVE-2019-8505: Ryan Pickren (ryanpickren.com)
TrueTypeScaler
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to initiate a Dictation request without user authorization
- Description: An API issue existed in the handling of dictation requests. This issue was addressed with improved validation.
- CVE-2019-8502: Luke Deshotels of North Carolina State University, Jordan Beichler of North Carolina State University, William Enck of North Carolina State University, Costin Carabaș of University POLITEHNICA of Bucharest, and Răzvan Deaconescu of University POLITEHNICA of Bucharest
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing a maliciously crafted font may result in the disclosure of process memory
- Description: An out-of-bounds read was addressed with improved bounds checking.
- CVE-2019-8517: riusksk of VulWar Corp working with Trend Micro Zero Day Initiative
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing maliciously crafted web content may lead to universal cross site scripting
- Description: A logic issue was addressed with improved validation.
- CVE-2019-8551: Ryan Pickren (ryanpickren.com)
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: A memory corruption issue was addressed with improved state management.
- CVE-2019-8535: Zhiyang Zeng (@Wester) of Tencent Blade Team
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: Multiple memory corruption issues were addressed with improved memory handling.
- CVE-2019-6201: dwfault working with ADLab of Venustech
- CVE-2019-8518: Samuel Groß of Google Project Zero
- CVE-2019-8523: Apple
- CVE-2019-8524: G. Geshev working with Trend Micro Zero Day Initiative
- CVE-2019-8558: Samuel Groß of Google Project Zero
- CVE-2019-8559: Apple
- CVE-2019-8563: Apple
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A sandboxed process may be able to circumvent sandbox restrictions
- Description: A memory corruption issue was addressed with improved validation.
- CVE-2019-8562: Wen Xu of SSLab at Georgia Tech and Hanqing Zhao of Chaitin Security Research Lab
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A website may be able to access the microphone without the microphone use indicator being shown
- Description: A consistency issue was addressed with improved state handling.
- CVE-2019-6222: Denis Markov of Resonance Software
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing maliciously crafted web content may disclose sensitive user information
- Description: A cross-origin issue existed with the fetch API. This was addressed with improved input validation.
- CVE-2019-8515: James Lee (@Windowsrcer)
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: A memory corruption issue was addressed with improved memory handling.
- CVE-2019-8536: Apple
- CVE-2019-8544: an anonymous researcher
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: A use after free issue was addressed with improved memory management.
- CVE-2019-7285: dwfault working at ADLab of Venustech
- CVE-2019-8556: Apple
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: A type confusion issue was addressed with improved memory handling.
- CVE-2019-8506: Samuel Groß of Google Project Zero
WebKit
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious website may be able to execute scripts in the context of another website
- Description: A logic issue was addressed with improved validation.
- CVE-2019-8503: Linus Särud of Detectify
Wi-Fi
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: Processing maliciously crafted web content may result in the disclosure of process memory
- Description: A validation issue was addressed with improved logic.
- CVE-2019-7292: Zhunki and Zhiyi Zhang of 360 ESG Codesafe Team
XPC
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A device may be passively tracked by its WiFi MAC address
- Description: A user privacy issue was addressed by removing the broadcast MAC address.
- CVE-2019-8567: David Kreitschmann and Milan Stute of Secure Mobile Networking Lab at Technische Universität Darmstadt
- Available for: iPhone 5s and later, iPad Air and later, and iPod touch 6th generation
- Impact: A malicious application may be able to overwrite arbitrary files
- Description: This issue was addressed with improved checks.
- CVE-2019-8530: CodeColorist of Ant-Financial LightYear Labs
Additional recognitionBooksCalendar
- We would like to acknowledge Yiğit Can YILMAZ (@yilmazcanyigit) for their assistance.
Kernel
- We would like to acknowledge an anonymous researcher, Peter Hempsall of 104days.com, and Sascha Mogler of mogler.com for their assistance.
Quick Look
- We would like to acknowledge Brandon Azad of Google Project Zero for their assistance.
Safari
- We would like to acknowledge Yiğit Can YILMAZ (@yilmazcanyigit) for their assistance.
Screen Time
- We would like to acknowledge Nikhil Mittal (@c0d3G33k) of Payatu Labs (payatu.com) for their assistance.
WebKit
- We would like to acknowledge Brandon Moore (@Brandonsecurity) for their assistance.
- We would like to acknowledge Andrey Kovalev of Yandex Security Team for their assistance.
Information about products not manufactured by Apple, or independent websites not controlled or tested by Apple, is provided without recommendation or endorsement. Apple assumes no responsibility with regard to the selection, performance, or use of third-party websites or products. Apple makes no representations regarding third-party website accuracy or reliability. Risks are inherent in the use of the Internet. Contact the vendor for additional information. Other company and product names may be trademarks of their respective owners.公開日:
iOS12.2へのアップデート手順と確認方法について
iPhone単体でのiOSのアップデート手順を紹介します。その他にiTunesからiOSのアップデートを行うことも可能です。iOS12.2へのアップデート手順
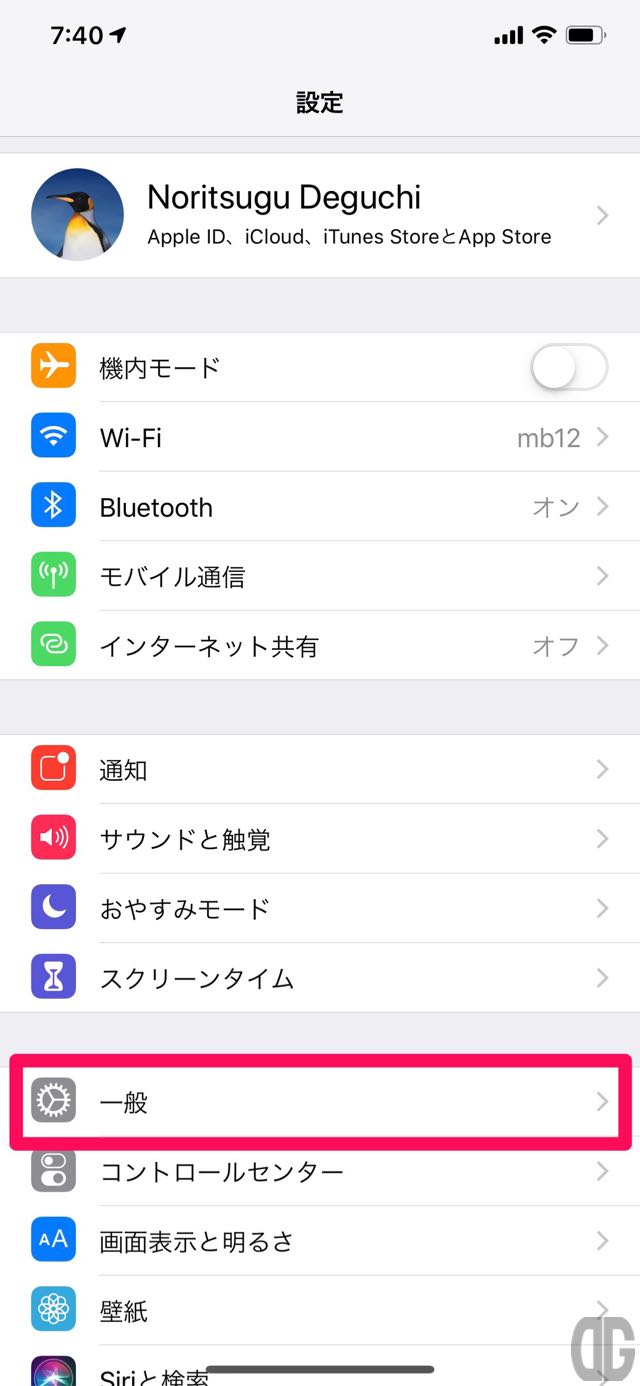
[timeline] [tl label=’手順 1′ title=’設定アプリの起動’] 「設定」アイコンをタップします。 [/tl][tl label=’手順 2′ title=’一般の選択’]
設定画面で「一般」をタップします。
[/tl][tl label=’手順 2′ title=’一般の選択’]
設定画面で「一般」をタップします。
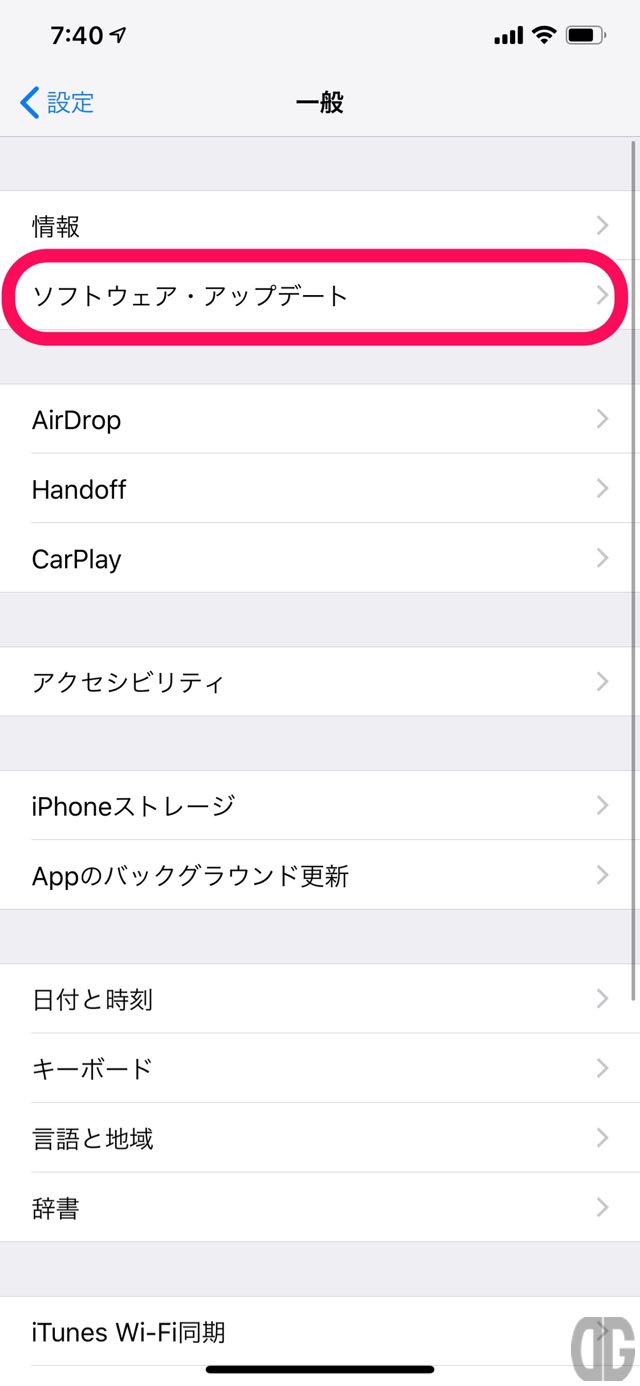
 [/tl][tl label=’手順 3′ title=’ソフトウェア・アップデートの選択’]
一般画面で「ソフトウェア・アップデート」をタップします。
[/tl][tl label=’手順 3′ title=’ソフトウェア・アップデートの選択’]
一般画面で「ソフトウェア・アップデート」をタップします。
 [/tl][tl label=’手順 4′ title=’ダウンロードとインストールの選択’]
ソフトウェア・アップデート画面で
[/tl][tl label=’手順 4′ title=’ダウンロードとインストールの選択’]
ソフトウェア・アップデート画面で
- iOS12.2であること
- ダウンロードサイズを確認
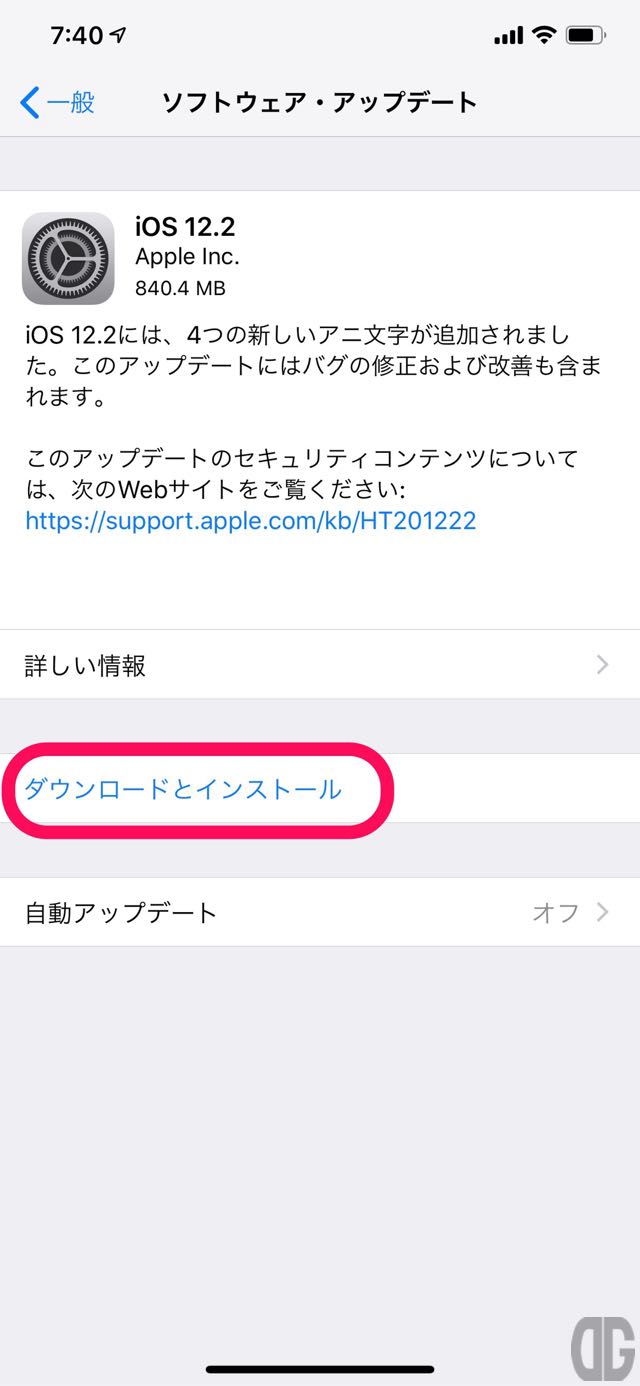 [/tl][tl label=’手順 5′ title=’パスコードの入力’]
パスコードを入力仮面でパスコードを入力します。
[/tl][tl label=’手順 5′ title=’パスコードの入力’]
パスコードを入力仮面でパスコードを入力します。
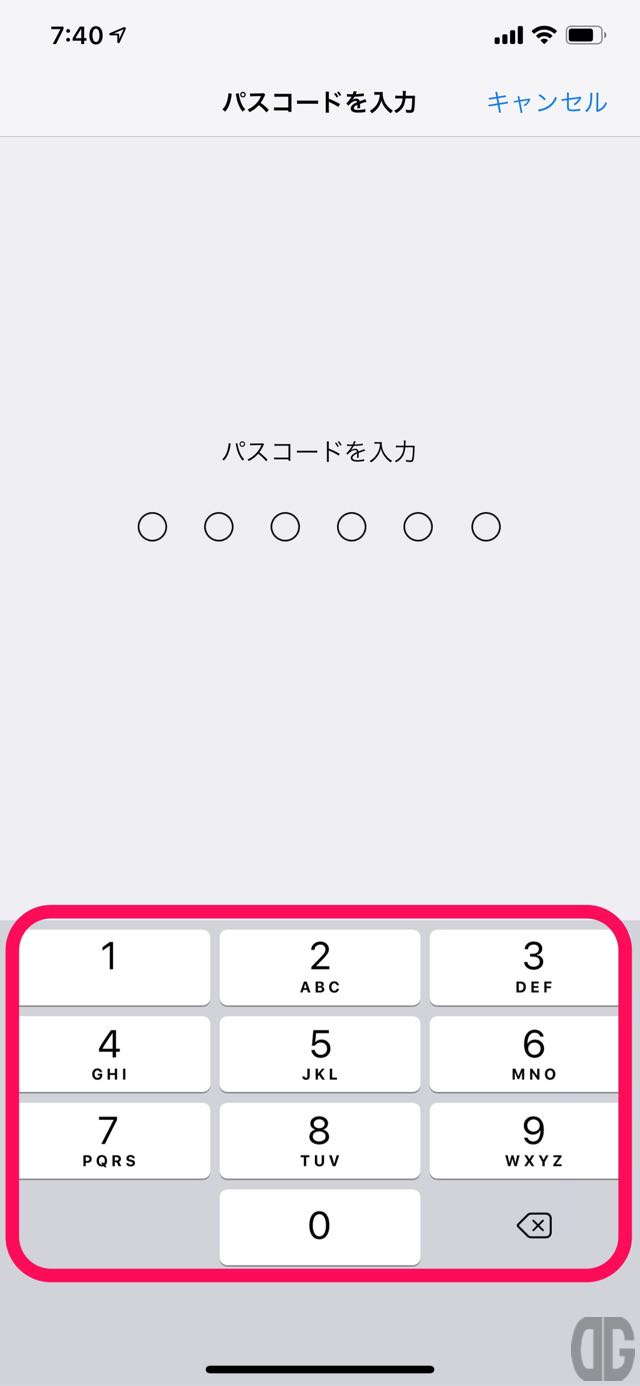 [/tl]
[tl label=’手順 6′ title=’ソフトウェアのダウンロード’]
自動的にソフトウェアのダウンロードが始まります。
[/tl]
[tl label=’手順 6′ title=’ソフトウェアのダウンロード’]
自動的にソフトウェアのダウンロードが始まります。
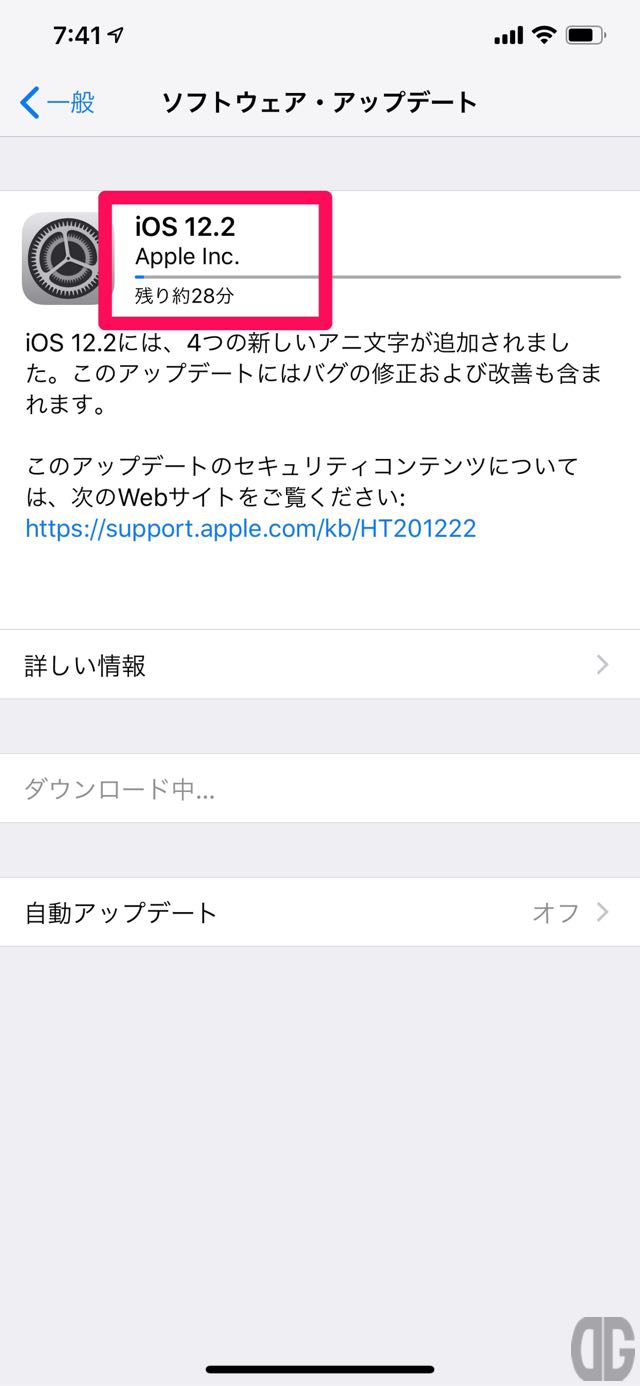 [/tl][tl label=’手順 7′ title=’今すぐインストールの選択’]
ダウンロードが終了すると確認画面が表示されるので、すぐにインストールする場合には「今すぐインストール」を選択します。
[/tl][tl label=’手順 7′ title=’今すぐインストールの選択’]
ダウンロードが終了すると確認画面が表示されるので、すぐにインストールする場合には「今すぐインストール」を選択します。
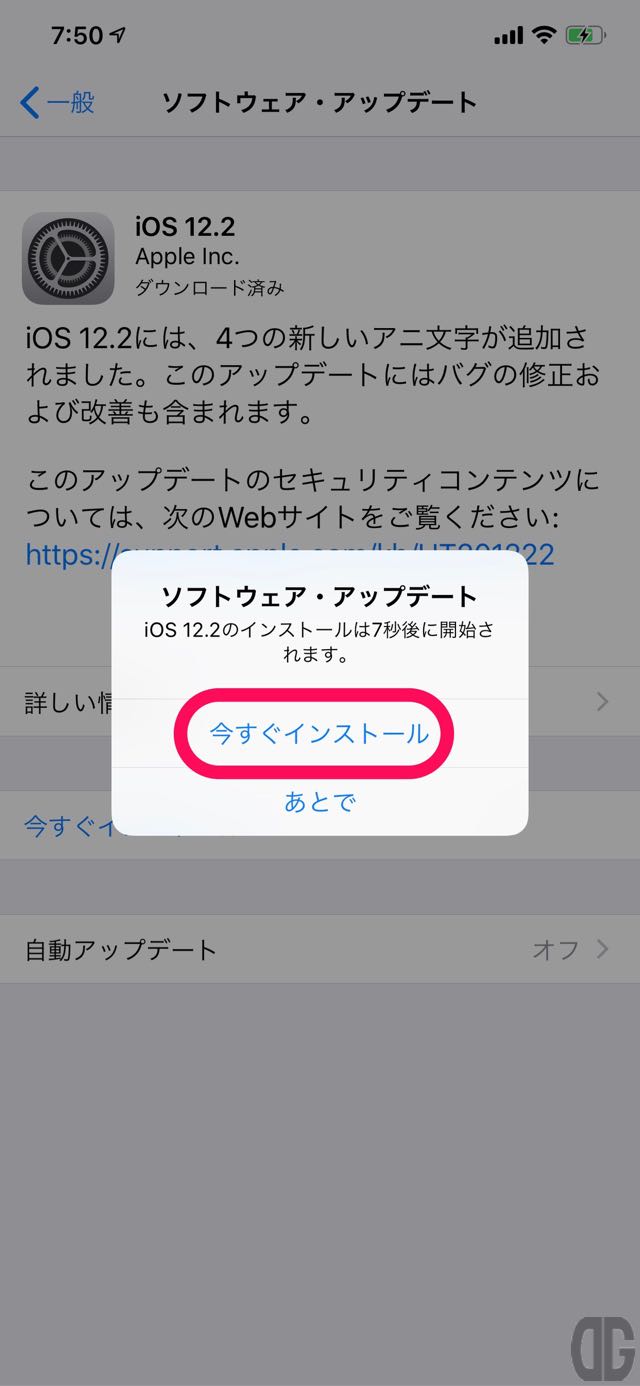 インストールする時間がない場合は「あとで」をタップしてアップデートを中断し、再度時間が確保できた際に「今すぐインストール」をタップし、インストールを行います。
[/tl][tl label=’手順 8′ title=’インストールと再起動’]
ファイルの確認が行われ、自動的に再起動とインストールが実施されます。
インストールする時間がない場合は「あとで」をタップしてアップデートを中断し、再度時間が確保できた際に「今すぐインストール」をタップし、インストールを行います。
[/tl][tl label=’手順 8′ title=’インストールと再起動’]
ファイルの確認が行われ、自動的に再起動とインストールが実施されます。
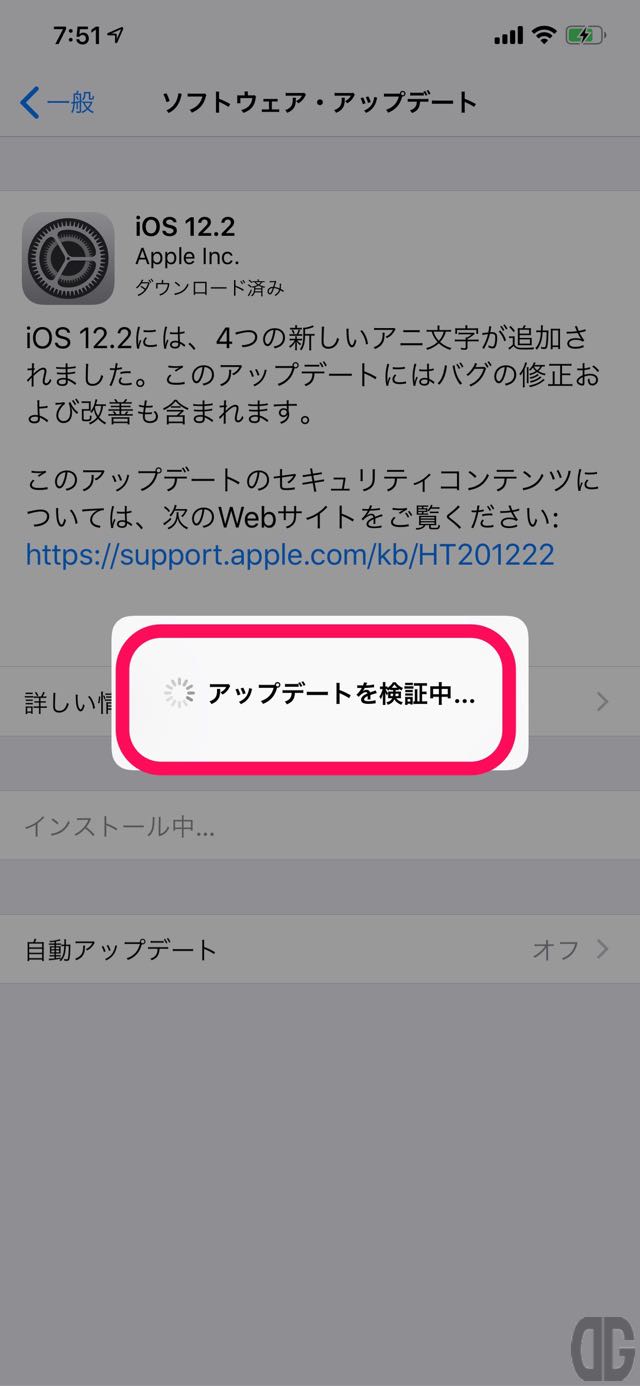 私が確認したときには再起動が2回実施されました。
[/tl][tl label=’手順 9′ title=’完了’]
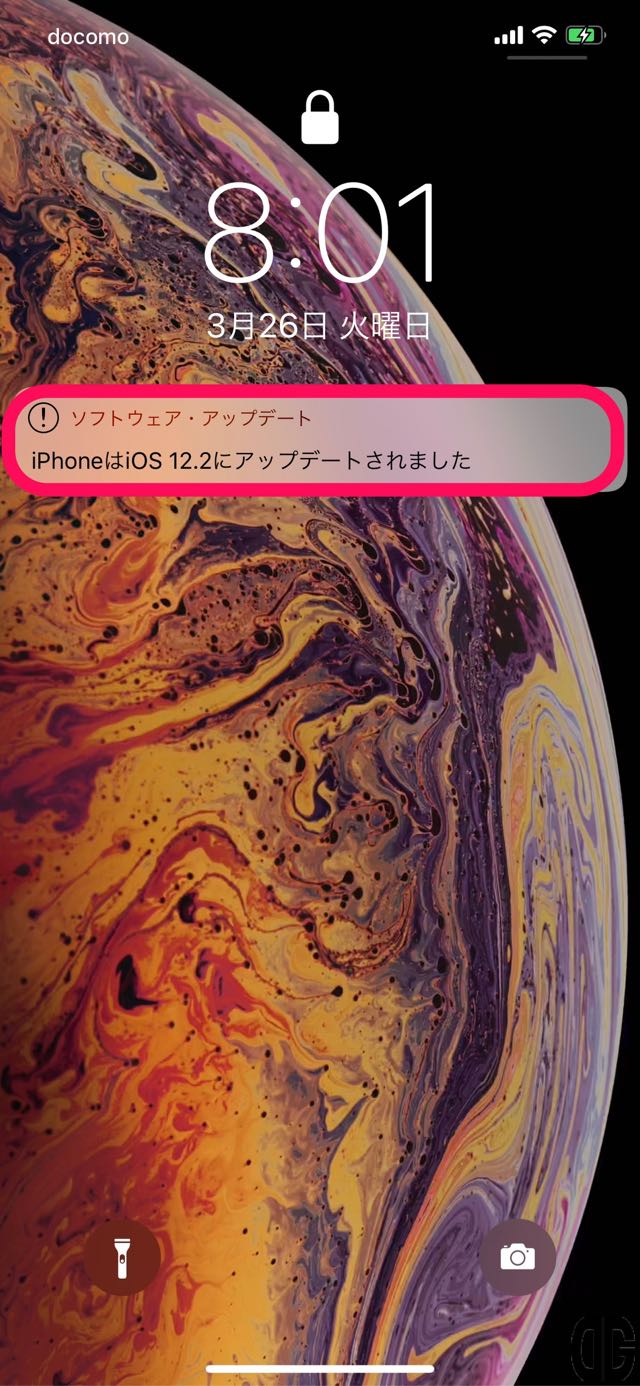
インストールが完了すると待受画面が表紙され、待受画面に「ソフトウェア・アップデート iPhoneはiOS12.2にアップデートされました」と表示されます。
私が確認したときには再起動が2回実施されました。
[/tl][tl label=’手順 9′ title=’完了’]
インストールが完了すると待受画面が表紙され、待受画面に「ソフトウェア・アップデート iPhoneはiOS12.2にアップデートされました」と表示されます。
 [/tl][tl][/tl][/timeline]
以上でアップデートは完了です。
[/tl][tl][/tl][/timeline]
以上でアップデートは完了です。
iOS12.2にアップデートされたことの確認方法(オプション)
待受画面が表示されればiOS12.2に更新されていますが、不安なときには次のように行います。ソフトウェア・アップデート画面での確認
[timeline] [tl label=’手順 1′ title=’「設定」アプリの起動’][/tl] [tl label=’手順 2′ title=’「一般」をタップ’][/tl] [tl label=’手順 3′ title=’「ソフトウェア・アップデート」をタップ’][/tl] [tl label=’手順 4′ title=’iOS 12.2であることの確認’] ソフトウェア・アップデート画面に「iOS 12.2 お使いのソフトウェアは最新です。」と表示されることを確認します。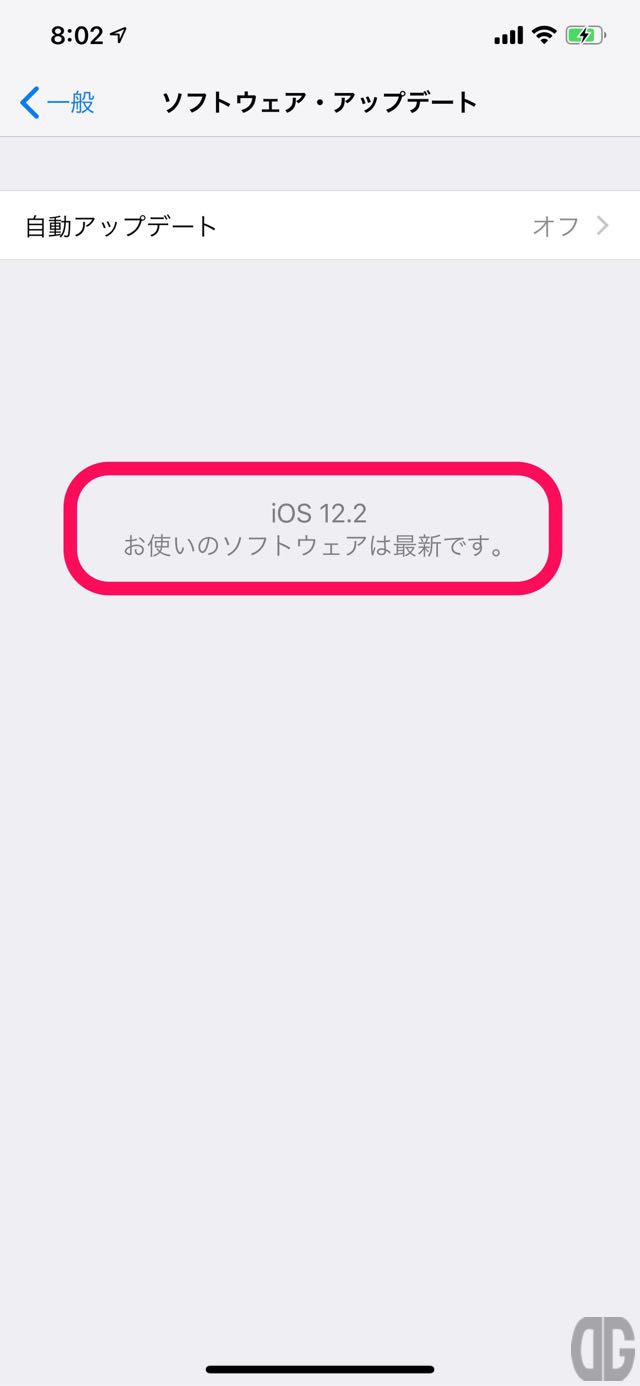 [/tl][tl][/tl][/timeline]
[/tl][tl][/tl][/timeline]
情報画面での確認
また、情報画面でもiOSのバージョンを確認できます。 [timeline] [tl label=’手順 1′ title=’「設定」アプリの起動’][/tl] [tl label=’手順 2′ title=’「一般」をタップ’][/tl] [tl label=’手順 3′ title=’「情報」をタップ’][/tl] [tl label=’手順 4′ title=’iOS 12.2であることの確認’] 情報画面のソフトウェアバーションに「12.2」と表示されることを確認します。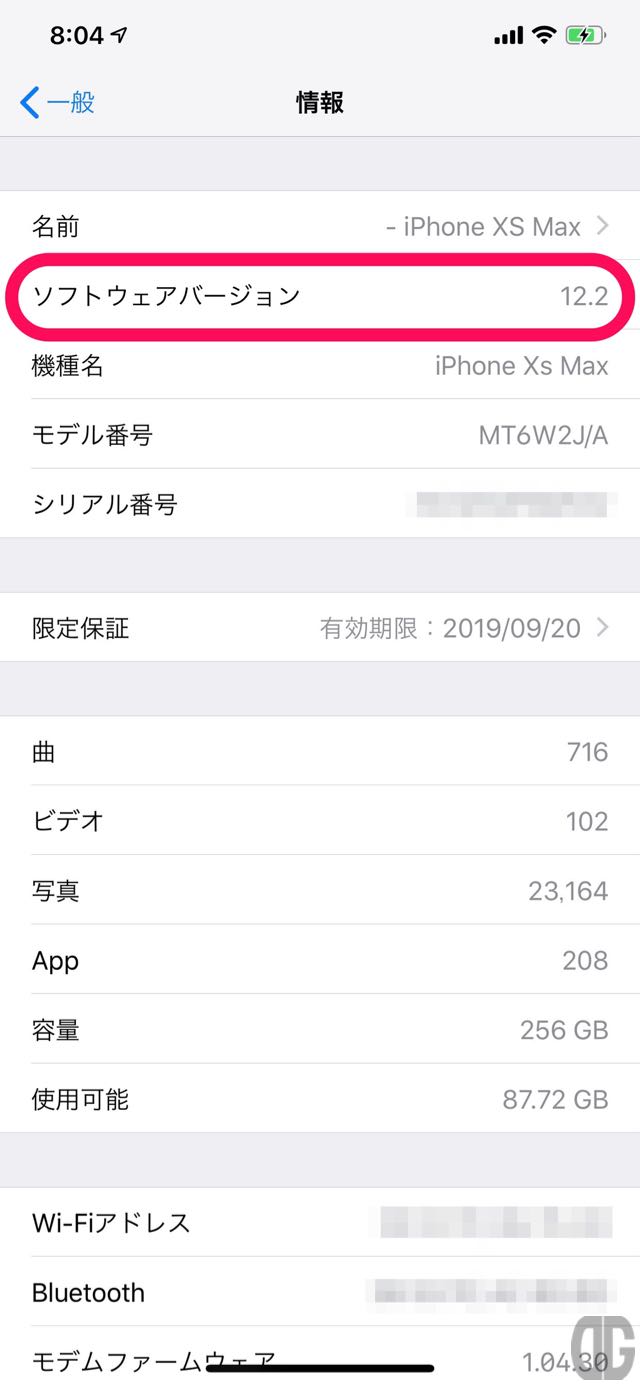 iOS 12.1.4まで確認できたより詳細なバージョン(ビルド番号)は「12.2」をタップすることで確認できます。
「12.2」をタップすると「12.2 (16E227)」と表示されます。
iOS 12.1.4まで確認できたより詳細なバージョン(ビルド番号)は「12.2」をタップすることで確認できます。
「12.2」をタップすると「12.2 (16E227)」と表示されます。
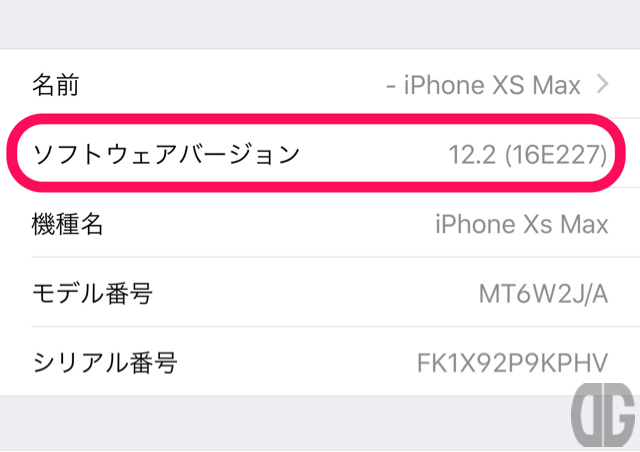 [/tl][tl][/tl][/timeline]
[/tl][tl][/tl][/timeline]
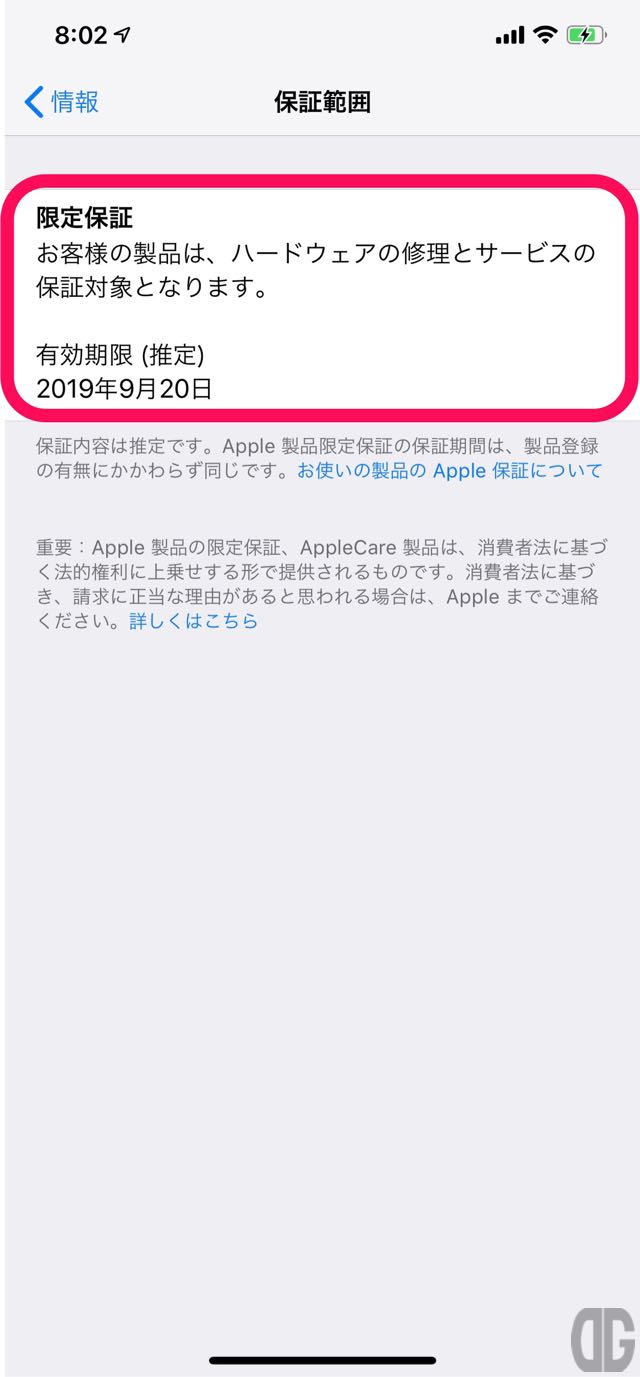
おまけ:iOS12.2新機能「限定保証」の確認
iOS12.2の新機能として「情報」に「限定保証」が表示されるようになりました。 それに伴い、情報画面の見え方(順序)が今までと大きく異なっています。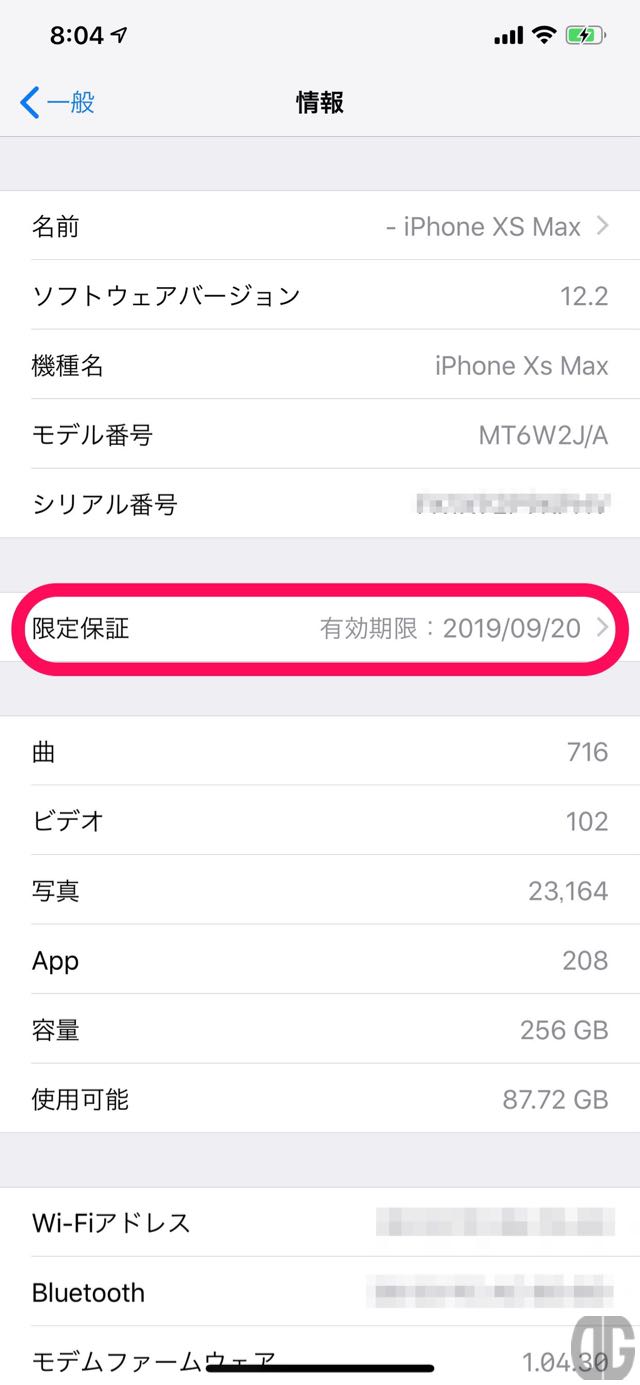 「限定保証」をタップすると保証範囲画面が表示され、「限定保証」の範囲、期間が表示されます。
「限定保証」をタップすると保証範囲画面が表示され、「限定保証」の範囲、期間が表示されます。